Critical Vulnerabilities in libxml2 (CVE-2025-49794, CVE-2025-49796): A Deep Dive and Seal Security's Proactive Solution
.png)
The cybersecurity landscape is constantly evolving, and the emergence of zero-day vulnerabilities poses significant challenges for organizations relying on widely used software components. Recently, two critical vulnerabilities, CVE-2025-49794 and CVE-2025-49796, were discovered in libxml2, a fundamental XML parsing library used across countless applications and systems, including popular containerized solutions like Confluent's Kafka. Rated with a severity of 9.1 by RedHat, these issues highlight the urgent need for robust and agile security solutions.
The discovery and initial disclosure
On June 3rd, 2025, security researcher Nikita Sveshnikov from Positive Technologies disclosed two critical vulnerabilities in libxml2. The details, including Proof-of-Concept (PoC) exploits and technical analyses, were made available on libxml2's GitLab repository (Issue #931 and Issue #933).
Unpacking CVE-2025-49796: A clear path to denial of service
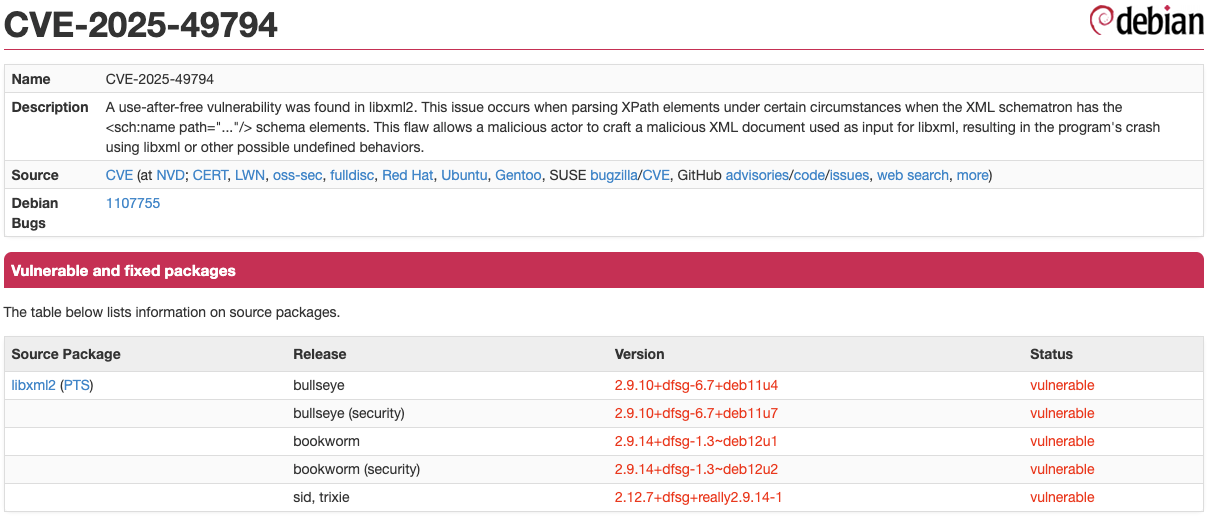
CVE-2025-49796 is a type confusion vulnerability found within libxml2's Schematron module. The root cause lies in the misinterpretation of a pointer returned from the XPath module. Specifically, the Schematron code incorrectly assumes the type of this pointer, leading to it accessing data as if it were a valid memory address. When the pointer contains the invalid value 0xffffffffffffffff, dereferencing it causes the program to crash, resulting in a Denial of Service (DoS).
The researcher provided information included a straightforward code snippet to address this specific vulnerability: verifying that the referenced pointer does not hold the invalid 0xffffffffffffffff value before access.
Delving deeper into CVE-2025-49794: UAF, type confusion, and a complex Fix
CVE-2025-49794 presents a more intricate scenario. Initially identified by the researcher as a use-after-free (UAF) vulnerability, further investigation revealed a deeper underlying problem. A proposed fix by Michael Mann addressed the UAF aspect, but critically, the PoC still caused system crashes. This indicated that the UAF was only one piece of the puzzle.
Our team at Seal Security conducted a thorough analysis and discovered that in addition to the UAF, there is a type confusion vulnerability on the same line of code as CVE-2025-49796. The xmlSchematronGetNode function can return multiple object types, all of which are cast to xmlNodePtr. This indiscriminate casting leads to significant confusion and allows for the exploitation of both the UAF and the type confusion.
Recognizing the compounded nature of this vulnerability, Seal Security crafted a comprehensive patch that addresses both the use-after-free and the type confusion. Our solution ensures the integrity of libxml2 by verifying the type of the result before attempting to access any additional attributes, preventing erroneous memory access and ensuring program stability.
The challenge for affected organizations
On June 11th, 2025, CVE numbers were officially assigned to both vulnerabilities. In accordance with libxml2's new security policy (Issue #913), the details of these critical issues were made public. While transparency is vital, it also means that millions of users are now aware of these high-severity vulnerabilities without readily available official patches. This is evident from the current state of affairs on the Ubuntu Security Tracker and RedHat Security Advisory, which at the time of this writing, do not yet include official fixes.

For organizations running Confluent Kafka containers, or any other system relying on libxml2, this situation presents a significant security risk. Waiting for upstream fixes can leave systems exposed to potential exploitation.
Seal Security's proactive approach
At Seal Security, we understand the critical need for immediate protection against zero-day threats. Our unique approach allows Seal Security customers to receive Sealed versions of vulnerable libraries like libxml2 that incorporate our expertly crafted patches, even when public fixes are unavailable.
By leveraging our deep understanding of software internals and vulnerability remediation, we empower our customers to proactively address critical security flaws, minimizing their attack surface and ensuring business continuity. In the case of CVE-2025-49794 and CVE-2025-49796, Seal Security's customers are already running secure versions of libxml2, shielded from these high-impact vulnerabilities.
The discovery of CVE-2025-49794 and CVE-2025-49796 in libxml2 underscores the dynamic nature of cybersecurity threats. While public disclosure is essential, the time lag for official patches can leave organizations vulnerable. Seal Security's ability to swiftly analyze, patch, and deliver solutions for vulnerabilities provides a crucial layer of defense, ensuring that our customers remain protected against the latest threats. Stay secure, stay proactive.
For more information schedule time with one of our experts.



.png)

