Fix CVEs in open source software without breaking your stack
Seal fixes unfixable vulnerabilities across the software supply chain with backported, in-place patches. By securing application dependencies, OS packages, and container images, Seal enables teams to reach audit-ready status faster without the risk of upgrades or breaking changes.
Secure, scalable patching across your entire open source stack
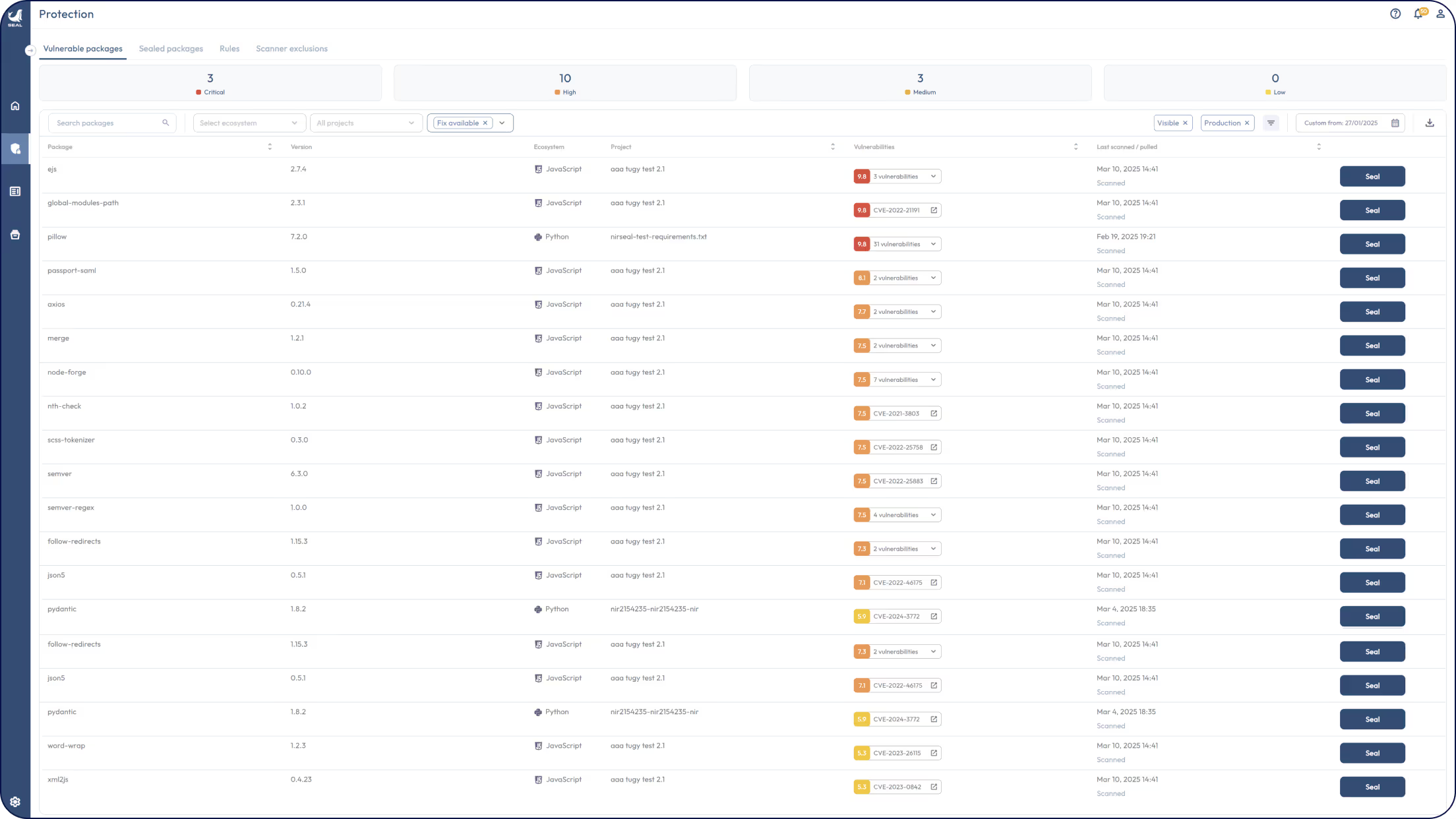
One platform to fix every open source vulnerability
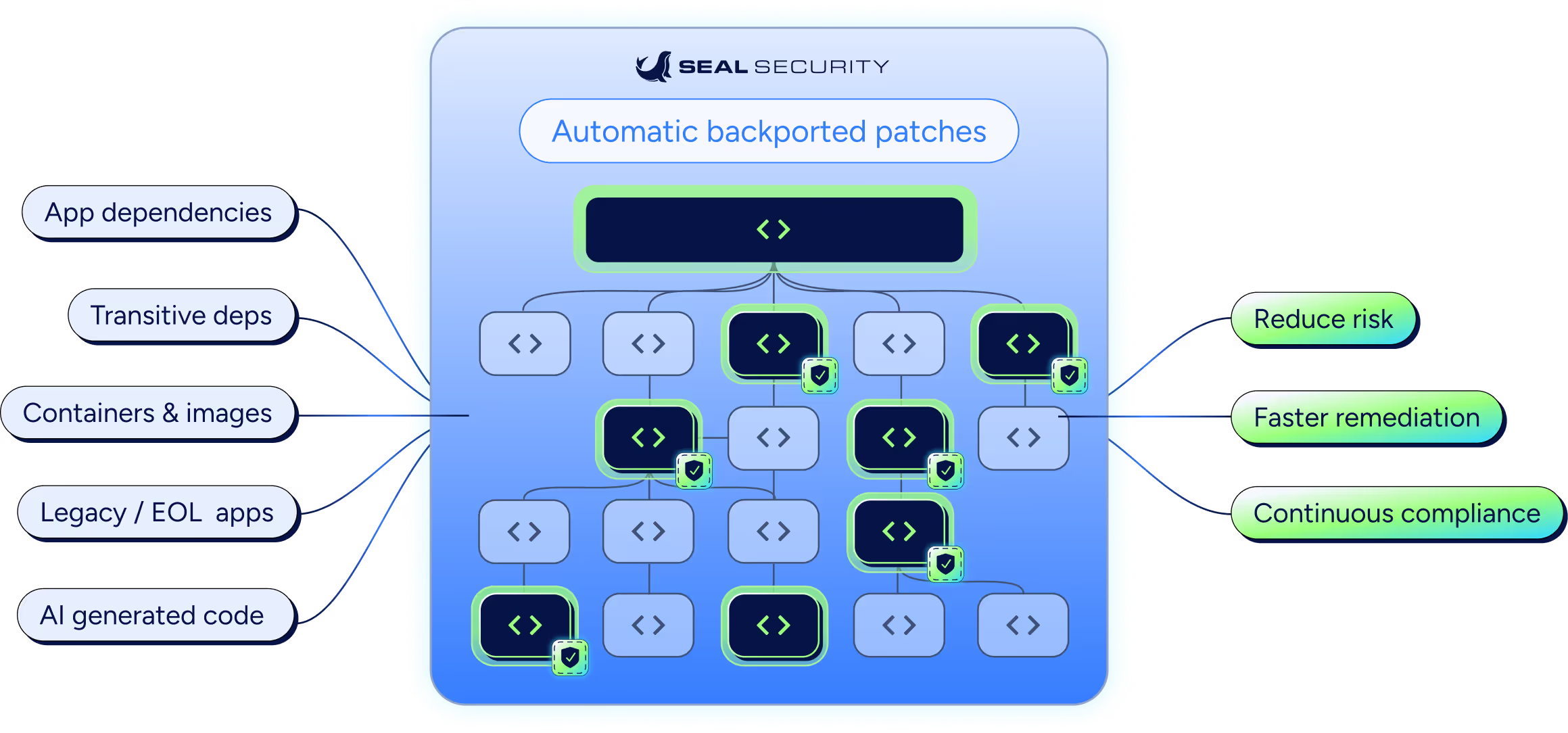
Why customers choose Seal Security
We’ll fix critical and high CVEs across your apps, OS, and containers, so you stay protected and compliant without upgrades or complex migrations.
Automated remediation with control
Patch CVEs in the versions you already run without draining engineering resources. Maintain full visibility through clear approvals and tracking, ensuring every change is verified and intentional.
No roadmap disruption
Patch in place to avoid the upgrades, migrations, and breaking changes that stall releases. By remediating vulnerabilities in parallel, your product teams stay focused on shipping features.
Shorten the exploitation window
Move from discovery to resolution in hours, not weeks. Seal delivers production-ready patches for critical and high vulnerabilities on a defined SLA, preventing security debt from sitting in your backlog.
Fix the “unfixable”
Remediate vulnerabilities in legacy, EOL, and hard-to-maintain components where upgrades are risky or impossible. Eliminate critical findings even when upstream maintainers have moved on.
Pass every security scan
Keep builds clean of critical and high findings across application dependencies, OS packages, and container images. Make scan outcomes predictable, repeatable, and easier to prove during customer reviews and audits.
Verified, traceable packages
Strengthen your supply chain with audited patches and clear provenance for every fix. Documented verification ensures you can trust what you ship and provide transparency whenever it is requested.
Latest research and publications
Frequently asked questions
Discover how Seal Security identifies and patches open source vulnerabilities without breaking changes.
Seal goes beyond traditional scanners by not only identifying CVEs in your source code management tools (e.g. GitHub, GitLab, and AzureDevOps), but also patching open source packages. Seal Security can also ingest scan results from popular SCA tools (e.g. Snyk and Black Duck) and widely used security tools (e.g. GitHub Advanced Security) and patch the CVEs in the open source packages.
Seal Security delivers backported security patches carefully engineered to apply only the minimal changes required to fix a vulnerability. All patches are built to be compatible with existing versions of open source packages with no added features or API modifications, ensuring maximum compatibility and minimal risk.
Seal Security uses community fixes with only the minimal necessary changes. All remediated versions undergo thorough testing and quality assurance, including manual inspection by our vulnerability research team and validation by a dedicated AI tool to ensure there are no breaking changes.
Since our platform runs at build-time, all of your existing tests run on our remediated version, providing an extra layer of assurance.
Seal supports all major distributions, including RHEL, CentOS, Alpine, and Debian.
Yes. Every image includes an SBOM (SPDX or CycloneDX format) and can be shipped with patch attestations and cryptographic signatures, making them ready for audit and continuous compliance workflows.
Seal Security supports all major languages including Java, Python, JavaScript, C/C++, Go, PHP, C#, and Ruby.
Seal helps organizations meet standards like FedRAMP, PCI DSS 4.0, NYDFS 500, HITRUST and DORA by delivering secure, sealed packages and images with SBOMs and patch attestations.
Seal Security handles all critical and high rated vulnerabilities within 72 hours of being made public.






.jpeg)