We fix them
Production-ready backported patches that fix CVEs in place, without upgrades, breaking changes, or R&D bottlenecks, whether your code was written by engineers or generated by AI
.avif)
.webp)
Security fixes on your timeline - no upgrades, downtime, or broken builds
No upgrade required
Patch vulnerabilities in the versions you’re already running. No breaking changes, no downtime, no technical debt.

Fix the “unfixable”
Secure transitive dependencies, EOL libraries, and legacy systems that scanners mark as "no fix available".

Compliance ready, always
Maintain continuous compliance with 72-hour remediation SLAs, no forced upgrades required.

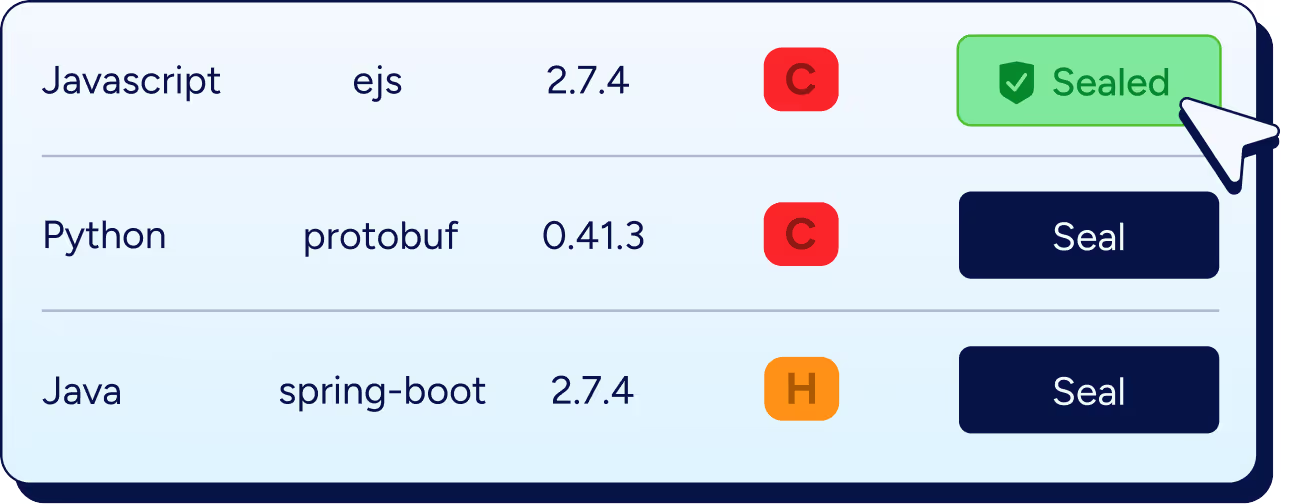
Fix open source vulnerabilities across your stack with one unified solution

Secure application dependencies
Patch direct and transitive dependencies in place, even the ones your scanner marks as “unfixable”.
Uphold compliance and meet customer SLAs
Pass every scan and meet every SLA for FedRAMP, PCI DSS 4.0, NYDFS, and customer audits.
Secure end-of-life environments
Keep CentOS, RHEL 6, and other EOL distros secure with post-EOL security patches.

Secure legacy and hard-to-manage code
Fix vulnerabilities in legacy apps and vendor-supplied software, even without source code access.
Secure your entire Linux infrastructure
Deploy backported fixes across containers, VMs, and bare metal without breaking upgrading your OS.
Why our customers love us

Secure your entire development lifecycle
Seal Security supports a wide range of languages and integrate smoothly with your tools, pipelines, and workflows to ensure seamless security at every step.
Latest research and publications
Frequently asked questions
Discover how Seal Security identifies and patches open source vulnerabilities without breaking changes.
Seal Security delivers one-click, backported, fully compatible patches for existing versions of open source packages. Seal identifies and fixes vulnerabilities across your entire stack, from application dependencies, to Linux packages within your containers in your production environments, to post-EOL bare metal devices. Seal’s approach reduces technical debt, prevents risk downtime, and helps teams ship faster, without breaking changes or compromising security and compliance posture.
Seal Security handles all critical and high rated vulnerabilities within 72 hours of being made public.
Seal Security streamlines audit-readiness and continuous compliance for FedRAMP, PCI DSS 4.0, NYDFS, HITRUST and DORA.
Seal Security supports all major languages including Java, Python, JavaScript, C/C++, Go, PHP, C#, and Ruby.
Seal Security integrates with GitHub, GitLab, and Azure DevOps. It also supports major SCA tools, like Snyk, BlackDuck, GitHub Advanced Security, Checkmarx, alongside vulnerability scanners such as Wiz, Trivy, StackRox, and Grype to automate remediation within your existing workflow.
Seal Security supports all major Linux distributions, including Red Hat Enterprise Linux (RHEL), CentOS, Alpine Linux, Debian, and Oracle Linux.
Seal Security is certified with SOC 2 Type II and ISO 27001.














.jpeg)