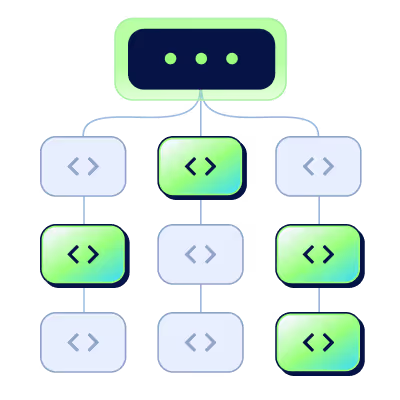
Eliminate the “unfixable”
Remediate vulnerabilities anywhere in your dependency tree with sealed packages that keep the same version and behavior, replacing only the vulnerable libraries and not their dependent frameworks.

Maintain security in the CI/CD environment
Integrate Seal directly into your pipeline to remediate vulnerabilities without slowing down deployments. Every package is signed, ensuring code integrity and seamless verification via CLI.

Meet compliance requirements effortlessly
Stay audit-ready with signed artifacts, SBOM lineage, and complete audit trails for every remediation action. Support compliance objectives like FedRAMP and PCI DSS 4.0, and provide evidence without extra manual work.